
disclaimer : The service described below is in public preview at the time of writing this blog!
As organisations quickly move towards the cloud approach to reap the benefits, it is quite important to keep the services protected from security threats leveraging the state-of-the-art technologies. Microsoft introduced a native security feature named Microsoft Defender for Cloud, which can be used as the Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) for Azure, on-premises, and multicloud resources like AWS and GCP.

The Microsoft Defender for Cloud offers multiple comprehensive defense services for the compute, data, and service layers of the environment:
This article talks about one of the Defender services - the Defender for Devops, which was recently announced by Microsoft. Let’s explore it!
Microsoft Defender for Devops bridge SecOps and DevOps with automated discovery across pipelines, starting with GitHub and Azure Devops, with more to come. This service is currently in public preview.
The principal capabilities of this service are:
It also lists out :
It uses Microsoft Security Devops(MSDO), which is a command line application that integrates static analysis tools into the development cycle. MSDO installs, configures and runs the latest versions of static analysis tools and it is data-driven with portable configurations that enable deterministic execution across multiple environments.
Below is the list of the open-source tools used by MSDO.
| Name | Language | License |
|---|---|---|
| Bandit | Python | Apache License 2.0 |
| BinSkim | Binary–Windows, ELF | MIT License |
| ESlint | JavaScript | MIT License |
| Credscan | Credential Scanner (CredScan) is a tool developed and maintained by Microsoft to identify credential leaks such as those in source code and configuration files. Common types: default passwords, SQL connection strings, Certificates with private keys | Not Open Source |
| Template Analyzer | ARM template, Bicep file | MIT License |
| Terrascan | Terraform (HCL2), Kubernetes (JSON/YAML), Helm v3, Kustomize,Dockerfiles, Cloud Formation | Apache License 2.0 |
| Trivy | Container images, file systems, git repositories | Apache License 2.0 |
Let’s take a look at how to configure Microsoft Devops defender for Azure Devops!
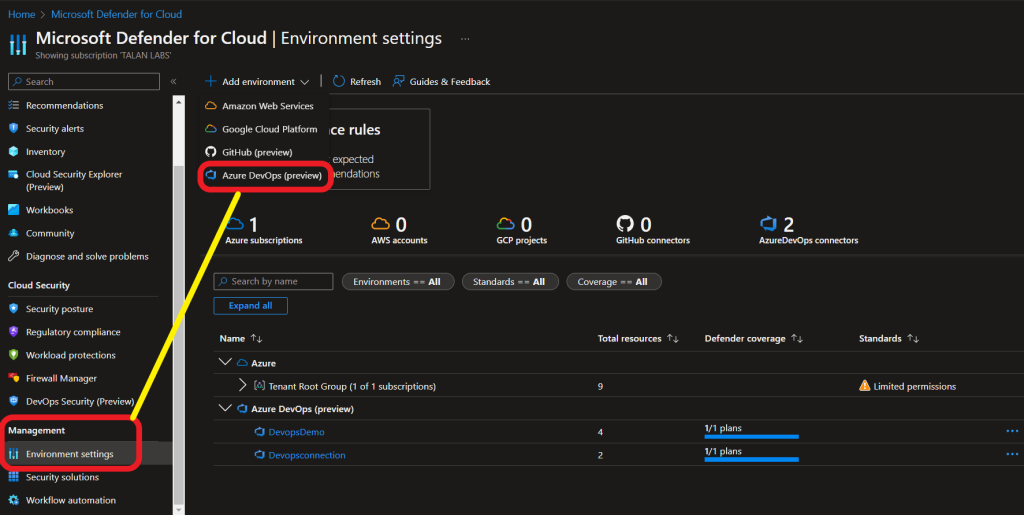
Login to your Azure portal and navigate to Microsoft Defender for Cloud.
Navigate to Environment Settings and select Azure Devops in Add Environment.
Fill in the connection name, Subscription and Resource group.
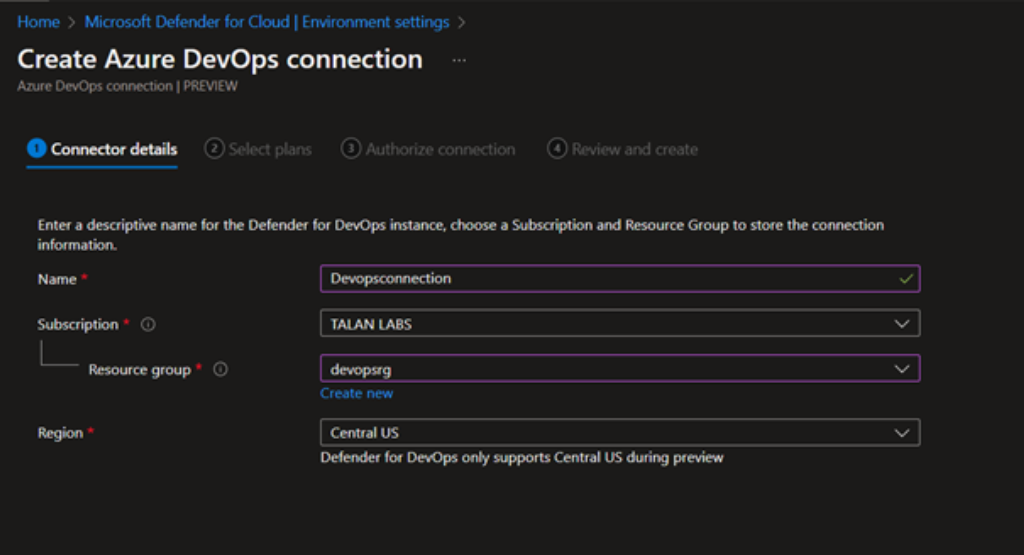
Select the Plan. Since this service is in public preview now, it is available as free of cost.
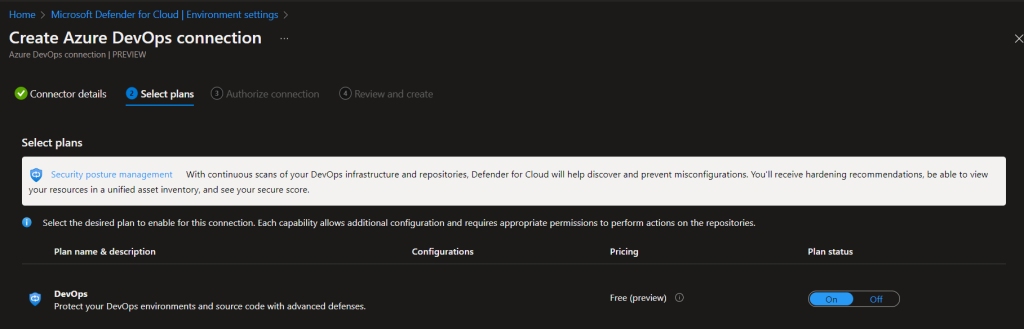
You have to authorize the connection to grant access to your Devops resources. Ensure you are selecting the correct Azure Devops profile while providing authorisation.
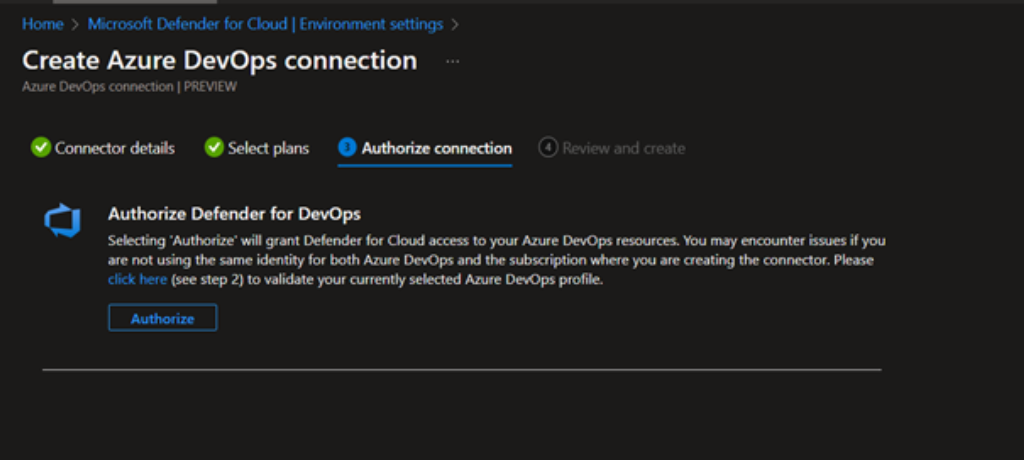
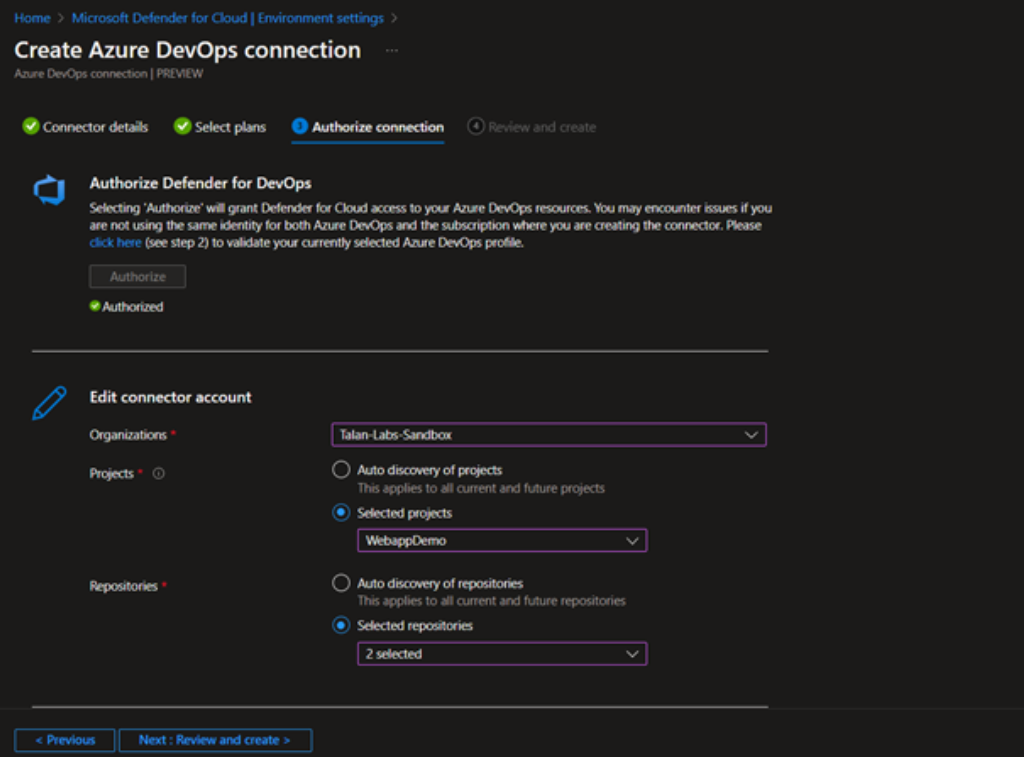
Once authorised, you can choose auto discovery or selected projects/repositories to apply the Defender for Devops service.
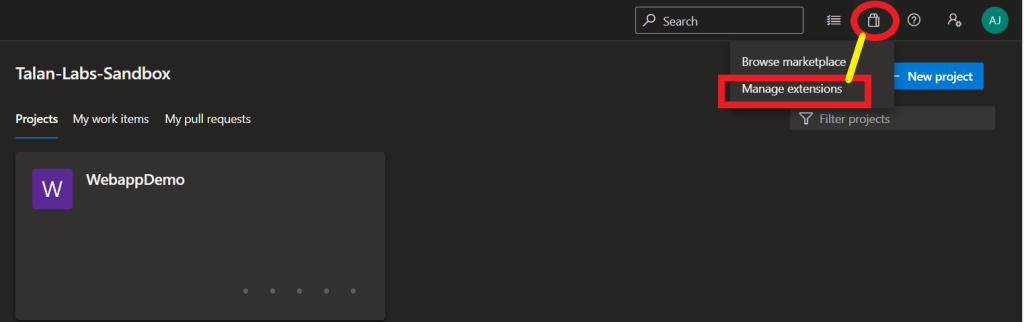
There is an extension for Azure DevOps named Microsoft Security DevOps Azure DevOps Extension which contributes a build task to run the Microsoft Security DevOps CLI.
Let’s see how to do this!
Log onto Azure Devops and select Manage Extensions from the Shopping Bag.
Search for the Microsoft Security Devops extension in Marketplace.
Select your Devops Organisation and install it.
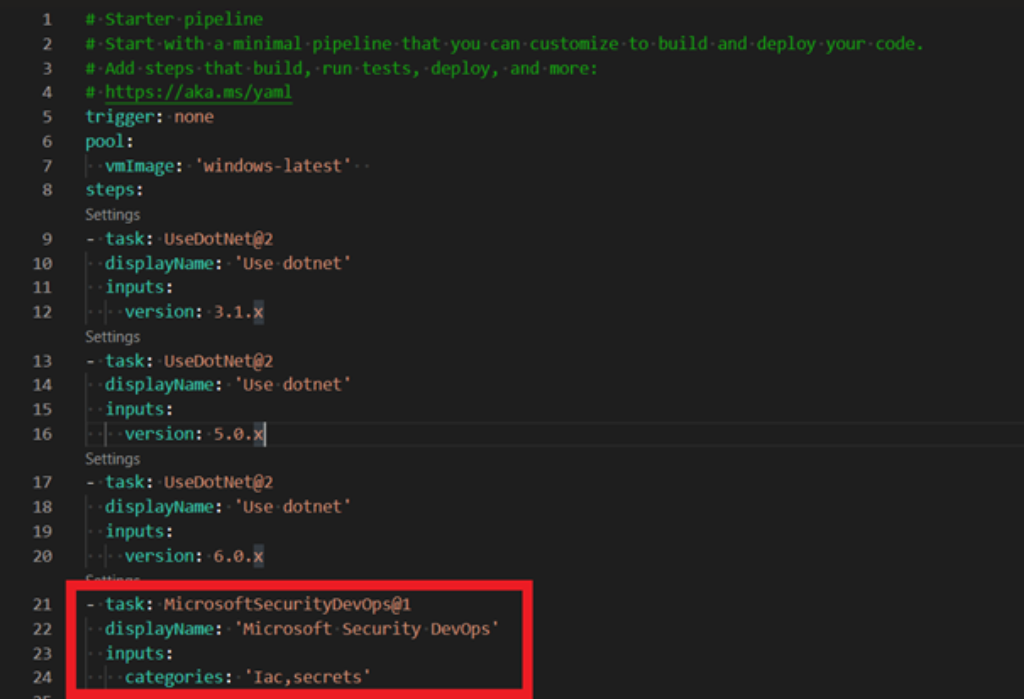
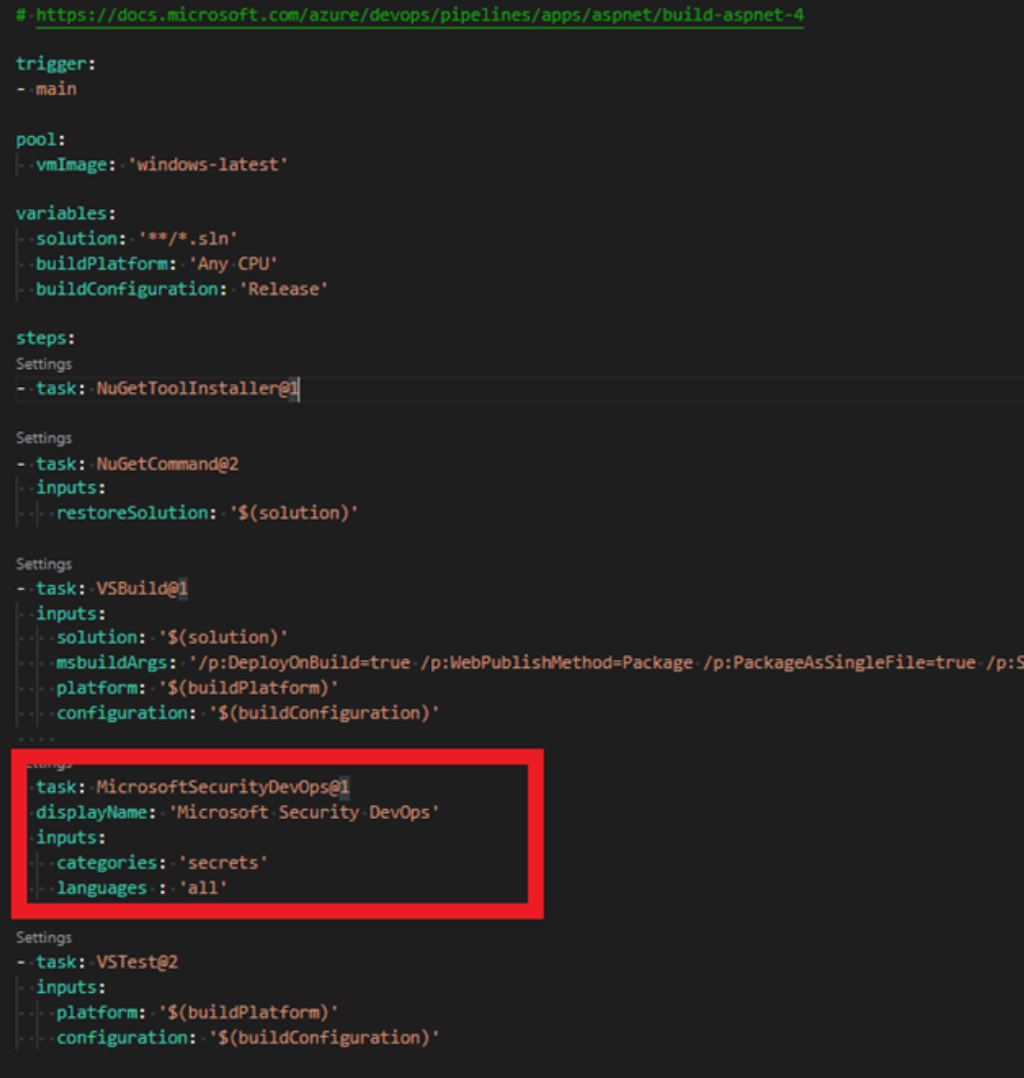
Add Microsoft Security Devops task in your yaml pipeline.
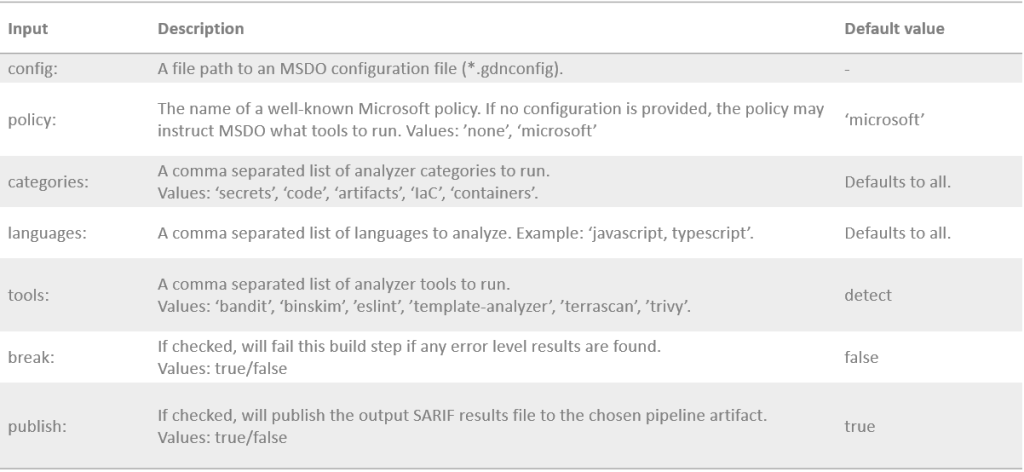
The inputs allowed for the MSDO task are given below :
If you would like to get the analysis results displayed automatically under the Scans tab, you have to install the extension SARIF SAST Scans Tab on your Azure DevOps organization.
Let’s look at a sample pipeline output which displays the Terrascan results under Scans tab. You can see the misconfigurations identified in the terraform Iac (Infrastructure as Code).
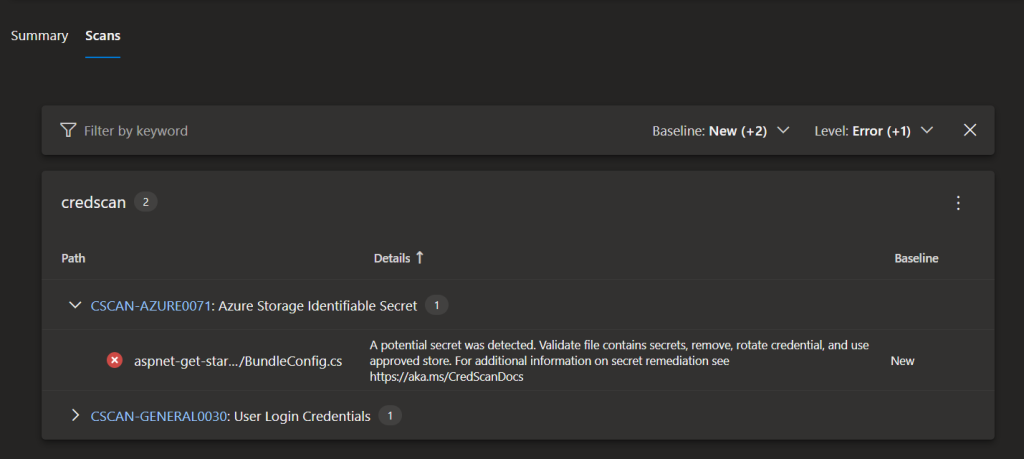
Now let’s look at a sample build pipeline output which displays the Credscan results under Scans tab. It identified the passwords that I have hardcoded in the source code. That’s awesome!
If you click on the results, you will see more details on the error.
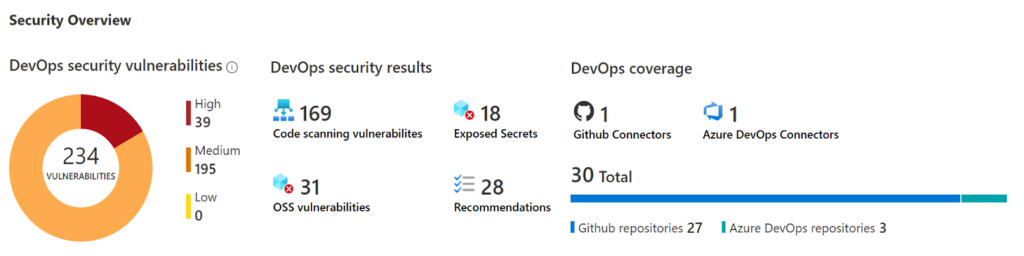
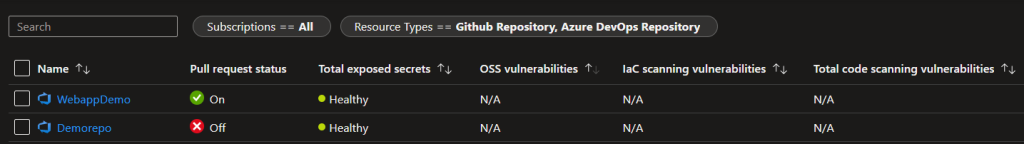
Microsoft Defender for DevOps unifies DevOps Security Management across multi-pipeline and multi-cloud environments. This feature helps to identify all vulnerabilities in your Azure Devops and Github repositories in a single dashboard which is very impressive.
Since this is in preview phase, we can expect many more updates here. If you are interested in learning more about this, check this out.
Hope you have learnt something new!
Cover Photo by Raphaël Cubertafon on Unsplash